-
Powershell based Plex “Local Player”
So, imagine a scenario where you’re trying to give a presentation on a customer’s PC, what you are trying to show is a video on a remote Plex server, but the customer’s PC is so locked down (whitelisted apps only) that whilst vlc will work, a web browser won’t! Seriously!!! However, powershell did work and…
-
Online Anonymity, Privacy and Risk Evaluation
I got into a conversation the other day about why I, as a massive supporter of the right to online privacy, still tended to use my real name online, in places where a more anonymous handle would be more than acceptable. You’d have thought as somebody quite proficient at OSINT (Open Source, Intelligence, the art…
-
InfoSec Posts
A change of circumstances means I am able to blog about InfoSec related topics again (having previously removed all the old posts) ! I’ll probably start with a few write-up of the InfoSec Pentest Challenges and CTFs I’ve done recently and them something on how to set up and ELK stack as a super-low-cost SIEM…
-
Disneyland Paris 1/2 Marathon (Part 3 – Race Day)
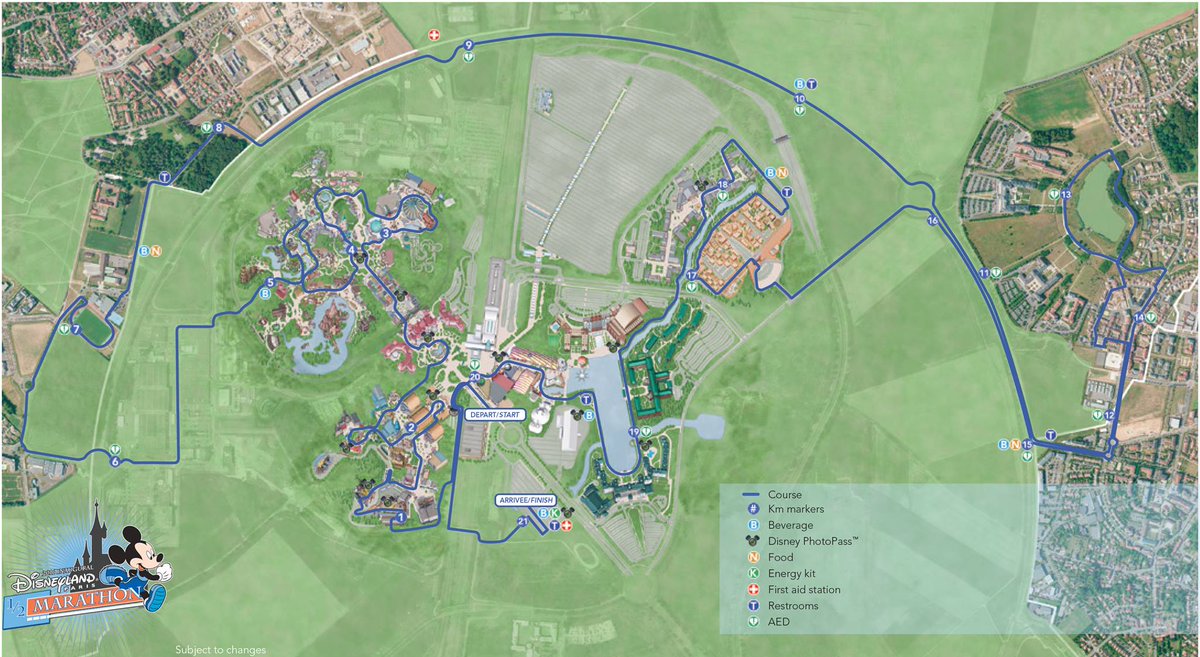
So, race day. Firstly, having to wake up at 5am for a race is no fun, waking up in a Cars themed hotel room and having somebody interrupt your race-day prep to take pictures even less so, especially when you know the photographer is going back to sleep for another few hours, hence the grumpy/asleep face…
-
Disneyland Paris 1/2 Marathon (Part 2 – Disneyland)

So, fast-forward a few weeks and I’m in Paris, up to now, bar one “bad” 13 mile Sunday training run (where I’d fallen apart at 8 miles) my preparation had gone great, well apart from two long days in Disneyland with super-excited three year old wanting to sit on my shoulders for hours on end…
-
Disneyland Paris 1/2 Marathon 2016 (Part 1 – The road to Disneyland)

So, Sarah from Pudsey Pacers asked me to do a write up of the Disneyland Paris 1/2 Marathon and as she’s kind enough to coach the group I run with twice a week, there was no way I could refuse. Important Note: This got massively long (so big I split it over 3 posts), if…
-
Nothing to see here
Don’t expect to find much here. I’m normally too busy doing stuff to write it up afterwards. Stuff that is currently taking up my time Being a dad and husband. Getting fit and slim again. I’m back running again and I’m on a serious diet for the first time ever. Taking my lifelong hobbyist interest in…

I remember when this was just a hompage
The random ramblings of Glenn Pegden